Joint effort for cybersecurity in smart buildings
Key actors are joining forces to contribute with guidance for the real estate, building and construction industry, to raise the level of...
3 min read
Pål André
Mar 14, 2023 12:15:19 PM

Most businesses produce either goods or services, or both. Manufacturers vary greatly - from critical national infrastructure to buildings and homes, food and other consumer services, and everything in between. Although the goods or services that are delivered may have particular requirements, most of us agree that there are basic components that make up the product or service being sold. Buildings and homes have walls and ceilings, groceries often comes in some type of package, and so on. Although walls, ceilings and packaging can have different shapes and colors, they are - ultimately – still walls, ceilings and packaging.
At the same time, history has taught us that properties, such as houses, are something that "individuals" - often criminals – may want to break into. Today's methods of protecting properties from burglary are often far more than simple door locks or walls made of fragile materials. But what is it that determines whether "someone" is allowed to enter a building or into a specific room? Is it because we trust them? Have they told us who they are? Do they have an errand?
To understand the history behind this, we must go back in time - and significantly further than you may think.
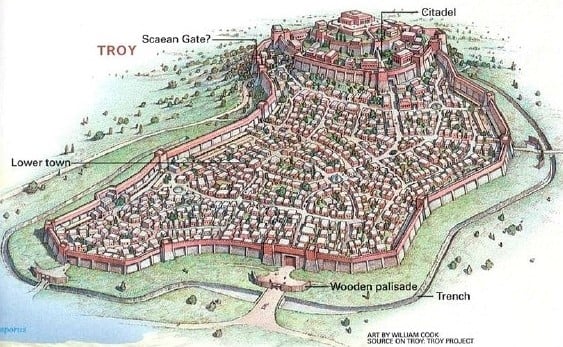
The image above is to represent the historic city of Troy in Asia Minor. The city, founded by Troy from Greek mythology, was home to the Trojans. Under Emperor Augustus (63 BC - 14 AD) the city was named Ilium. Troy as a city was rebuilt several times, from 3000 years BC. to the 1st century BC. However, the most famous reference point in time is most often associated with the Trojan War (1200-1300 BC), where the Greeks took over the city with the help of the Trojan horse and the Greek hero Achilles' wrath. As the picture above shows, the city was built with several security measures, including a moat and trench, wooden palisades, and high walls both around the city and the castle. As the story goes, it was enough for the Greeks to play on the Trojans' trust and respect for the horse, whereupon they managed to trick the Trojans into accepting a gift (i.e., a Trojan horse), which unfortunately for the Trojans was filled with Greek warriors. Immediately after the Trojans had brought the hollow horse figure within their city walls, the Greeks laid the whole city in ruins and killed everything and everyone in their path.
Although the city of Troy was built according to all the best practices and advice of the time, the city walls were still not strong enough to withstand the human ability to "trust someone."
In IT security, this story is used to argue for what is referred to as "perimeterless security" or the "zero trust model" (i.e., Zero Trust). The argument for Zero Trust is quite simple, namely that we cannot solely base our security measures on hard perimeters. The traditional approach with hard perimeters is in direct conflict with modern business models, where interaction, sharing and close integrations characterize digital development. Through its daily work with customers, Defendable still sees that many have great faith that security is formed in technological gadgets and networks, and that this "automagically" creates Zero Trust. Defendable has a different view, where Zero Trust must rather be interpreted as a strategic framework that considers context-based and process-centric security.
In 2007, the Jericho Forum Commandments was formalized as a result of the lack of public discussion about perimeterless security. Four of their commandments are listed below:
You can no longer rely on the network to protect data or information within an application. The data security must be moved closer to where the data occurs. This often means that one or more of the following measures should be implemented:
The focus should in any case turn in a strategic direction, where trust modelling and "Never Trust, Always Verify" become core components in how to secure data within the business. At the same time, the network should safeguard other values for the business, such as uptime.
Defendable is now building a market-leading security architecture team. The team will, among other things, help our customers establish Zero Trust architectures, as part of the company's holistic approach to cyber and information security. In this way, the chance is reduced that customers in particular, and society in general, are tricked - often based on excessive respect and false trust - into accepting hollow horses filled with attackers with evil intentions and subsequent costly repercussions.

Key actors are joining forces to contribute with guidance for the real estate, building and construction industry, to raise the level of...

There is a strong emphasis on IT security in society today, with companies investing significant resources in securing systems against malware,...