Security
Monitoring
Operational insight into what goes on within your IT infrastructure is crucial to control your cyber risk.
Managed detection & response
Effective cyber defense starts by forming an understanding of the threat landscape, how attackers can strike and by knowing your own vulnerabilities.
Defendable’s MDR service utilizes cyber intelligence and vulnerability assessment as a basis for detection and response.
The investigation, tuning and assessments made by Defendable’s experienced cybersecurity team, combined with automated processes, provide the optimal mix for early detection and fast response.
Defendable’s MDR service is a 24/7 service which can both be optimized for organizations using Microsoft 365 products, including Sentinel, and as a stand-alone solution.
Flexible configurations and multiple options
Defendable actively encourages customers to collect and retain as much relevant security log data as possible, as more data allows us to better detect and investigate incidents. However we recognize that the collection and storage of more log data comes with an increased cost.
Customers can choose to store additional log data in their own tenant using Microsoft Log Analytics or for a more cost-efficient solution, customers can also store log data in Defendable’s own log management platform.
Defendable’s MDR service comprises an up to date collection of detection and response methods, which can be supplemented by working with customers on developing specific detection and response actions for particular assets, users or security scenarios.
How it works
Take a deep dive into our MDR service.
Defendable SOC
 The heart of Defendable’s MDR service is the Security Operations Centre (SOC), where security analysts monitor and respond to threats 24/7, 365 days a year.
The heart of Defendable’s MDR service is the Security Operations Centre (SOC), where security analysts monitor and respond to threats 24/7, 365 days a year.
Depending on the severity of an incident, a dedicated Incident Response analyst or an entire Incident Response Team, may be mobilized to assist customers in the investigation, containment, eradication and recovery from a serious incident.
Defendable has SOCs in Oslo and Gjøvik for geo-redundancy
-
CTI
 Together with vulnerability assessment, CTI is the key to achieving effective cyber defence.
Together with vulnerability assessment, CTI is the key to achieving effective cyber defence.
Defendable monitors various open and proprietary threat intelligence feeds and utilizes these to find suspicious events and incidents on customer networks.
Defendable also extracts CTI from the dark web where leaked or stolen information is shared and traded. Dark web surveillance can give early warning of planning of attacks on a particular organisation or supply chains. -
SIEM & SOAR
 Defendable converts threat intelligence and vulnerability analysis into collections of Microsoft Sentinel Security Information and Event Management (SIEM) workbooks and Security Orchestration and Automated Response (SOAR) playbooks.
Defendable converts threat intelligence and vulnerability analysis into collections of Microsoft Sentinel Security Information and Event Management (SIEM) workbooks and Security Orchestration and Automated Response (SOAR) playbooks.
Workbooks provide our customers with a high-level overview of security events and trends in the organisation, whilst playbooks trigger automated response or enrichment processes when alerts or incidents are detected. -
Vulnerability analysis
 Defendable combines the functionality in Microsoft Defender and conducts regular vulnerability scanning to discover vulnerabilities in exposed services for our customers.
Defendable combines the functionality in Microsoft Defender and conducts regular vulnerability scanning to discover vulnerabilities in exposed services for our customers.
This activity is important to identify and close security holes before they can be exploited by threat actors.
Scanning is performed with market leading tools which are continuously updated with the latest vulnerability signatures. -
Threat hunting
 In parallel with SIEM and SOAR operations, Defendable performs proactive threat hunting in customer environments.
In parallel with SIEM and SOAR operations, Defendable performs proactive threat hunting in customer environments.
Defendable analysts will actively look for signs of malicious activity where static detection mechanisms have not yet been developed, and have been missed by tools such as Microsoft Defender.
Onboarding and operations
Defendable has a well-defined process for onboarding new organizations to the MDR service.
1. IDENTIFY
Type and number of endpoints and users that shall be monitored.
2. PLAN
How to monitor and perform response to incidents for the various types of endpoints and users.
3. ESTABLISH
Ensuring the right data is available in Defendable’s MDR platform. This could for example, involve connecting your instance of Microsoft Sentinel to Defendable’s MSSP tenant via Microsoft Lighthouse.
4. EXECUTE
Improve detection and response mechanisms based on new threat research, intelligence and vulnerability analysis.
Calibrate the detection mechanisms for an optimal true-false positive ratio.

Analyse, Contain, Eradicate, Recover and Report any incidents.
Monitor 24/7 and Threat hunt from the SOCs in Oslo and Gjøvik.
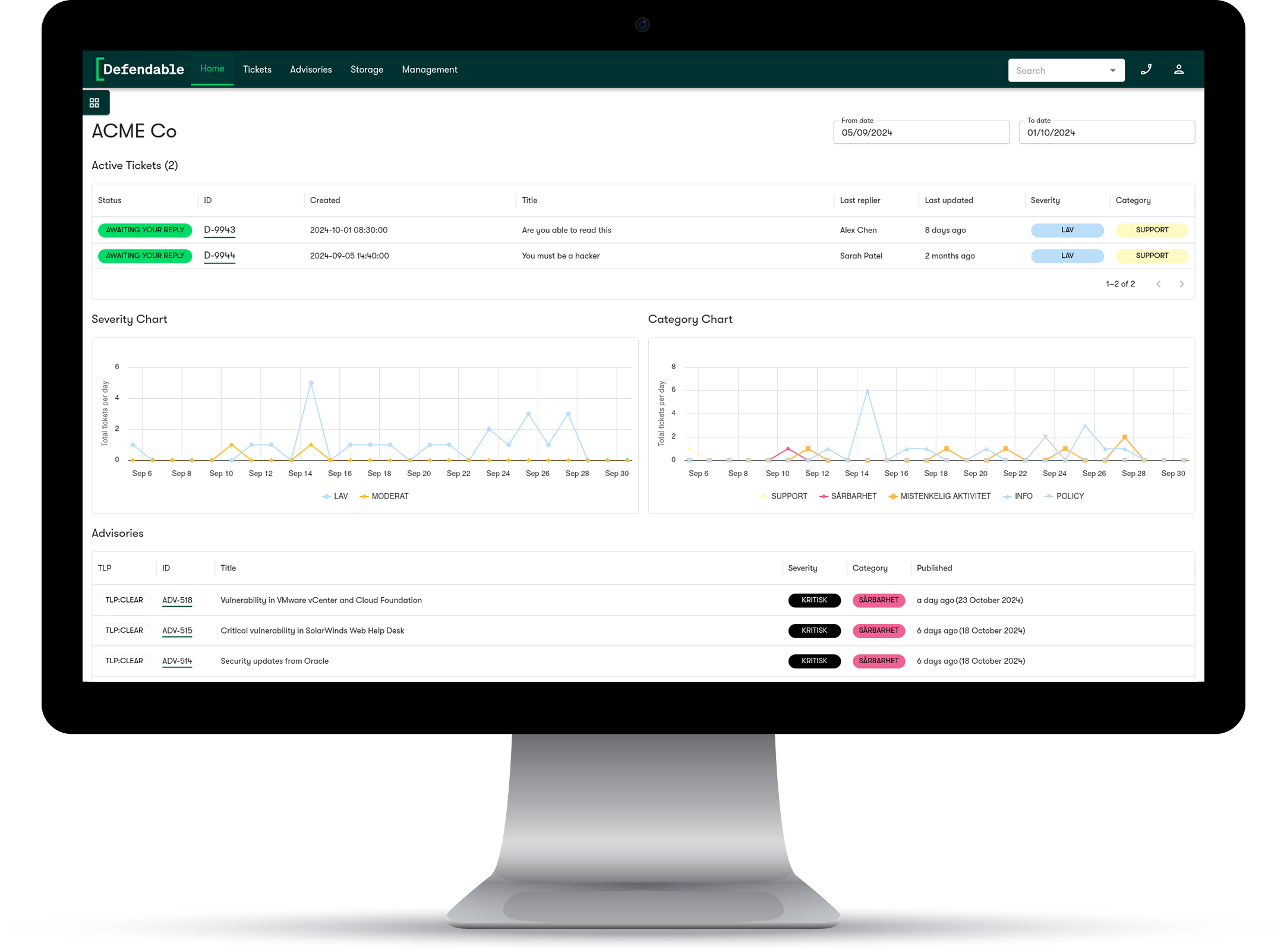
Customer Portal
Normal communication between Defendable SOC and customers happens through a portal where customers can follow the creation and management of tickets and receive vulnerability advisories and threat intelligence reporting.
Talk to us about your MDR needs